Happy Monday! ☀️
Welcome to the 648 new hungry minds who have joined us since last Monday!
If you aren't subscribed yet, join smart, curious, and hungry folks by subscribing here.

📚 Software Engineering Articles
One line of code caused $8,000 loss; learn from this mistake
Essential guide to DNS architecture and how it works
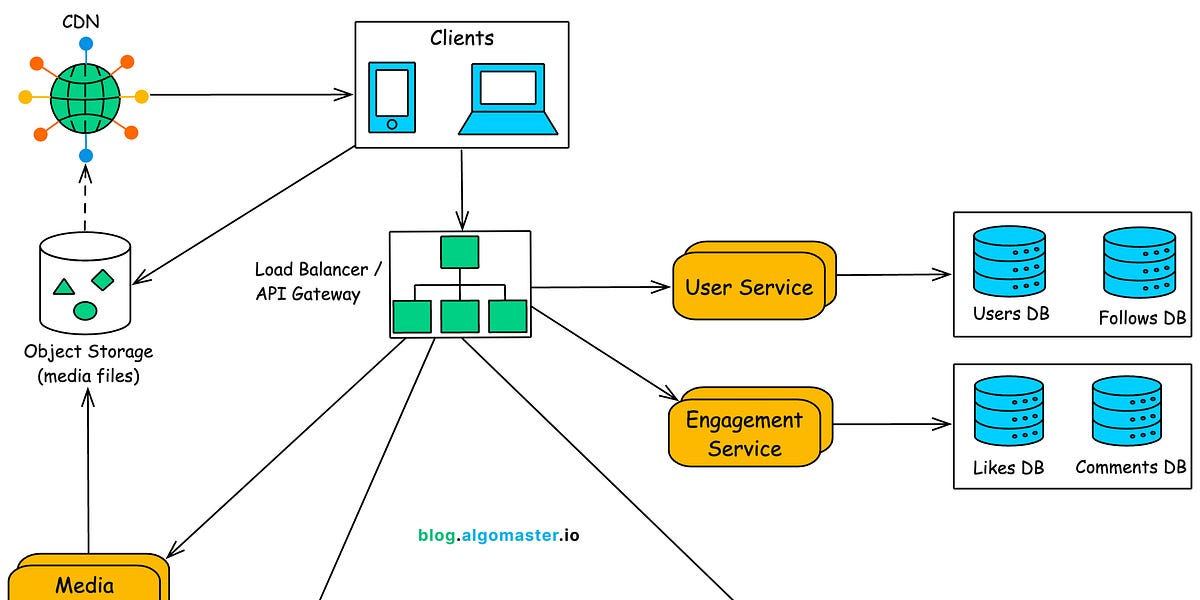
Designing news feeds that scale to millions of users
Engineer's guide to soft skills from Apple and Slack
Best practices for building performant Expo applications
🗞️ Tech and AI Trends
Amazon challenges SpaceX with first Kuiper satellite launch
ChatGPT adds product browsing to its capabilities
Claude expands reach with new enterprise integrations
👨🏻💻 Coding Tip
Use Rust's derive macros for type-safe database schemas and validations
Time-to-digest: 5 minutes
Big thanks to our partners for keeping this newsletter free.
If you have a second, clicking the ad below helps us a ton—and who knows, you might find something you love.
💚
How can AI power your income?
Ready to transform artificial intelligence from a buzzword into your personal revenue generator
HubSpot’s groundbreaking guide "200+ AI-Powered Income Ideas" is your gateway to financial innovation in the digital age.
Inside you'll discover:
A curated collection of 200+ profitable opportunities spanning content creation, e-commerce, gaming, and emerging digital markets—each vetted for real-world potential
Step-by-step implementation guides designed for beginners, making AI accessible regardless of your technical background
Cutting-edge strategies aligned with current market trends, ensuring your ventures stay ahead of the curve
Download your guide today and unlock a future where artificial intelligence powers your success. Your next income stream is waiting.

In a web landscape dominated by bots, protecting your server from malicious actors requires creative solutions. Here's how a simple compression technique can be turned into an effective defense mechanism against harmful bots that spam, scrape, or attempt to hack your server.
The challenge: Defend against automated attacks while maintaining server performance and legitimate user access, without complex infrastructure changes.
Implementation highlights:
Exploit gzip compression: Use web's native compression feature to serve specially crafted compressed files
Strategic detection: Implement middleware to identify malicious patterns and blacklisted IPs
Gradual response: Serve different-sized zip bombs (1MB -> 10MB) based on threat level
Memory exhaustion: Force bots to decompress small files into massive ones (1MB -> 1GB)
Simple integration: Add a few lines of code to your existing server middleware
Results and learnings:
Highly effective: Most malicious bots never return after encountering the zip bomb
Resource efficient: Only costs 1-10MB of bandwidth per blocked attack
Low maintenance: Once implemented, runs automatically with minimal oversight
The beauty of this approach lies in its simplicity: using a standard web feature as a defensive weapon. While not foolproof, it's remarkably effective against unsophisticated attacks that plague most websites.
Remember: The best defense sometimes isn't a wall, but a trap door that leads to a memory overflow! 🧨

ARTICLE (AI won't steal your brain)
Avoiding Skill Atrophy in the Age of AI
ESSENTIAL (humans > robots)
Mastering The Human Side Of Engineering: Lessons From Apple, Palantir And Slack
GITHUB REPO (fast like lightning)
Lightning-fast and Powerful Code Editor written in Rust
GITHUB REPO (browser independence day)
Truly independent web browser
ARTICLE (no more laggy apps)
Best Practices for reducing lag in Expo apps
ARTICLE (Meta knows your data)
How Meta understands data at scale
ARTICLE (solo dev wins)
The One-Person Framework in practice
ARTICLE (oops, $8k gone)
One line of code that did cost $8,000
ARTICLE (CSS showdown)
Tailwind vs Linaria: Performance Investigation
ARTICLE (React Query magic)
Concurrent Optimistic Updates in React Query
Want to reach 180,000+ engineers?
Let’s work together! Whether it’s your product, service, or event, we’d love to help you connect with this awesome community.

Brief: Claude now connects to 10+ apps like Jira, Zapier, and Intercom via Integrations, while its Research mode can scour the web, Google Workspace, and linked tools for 45-minute deep dives with citations.
Brief: OpenAI introduces a product-browsing feature in ChatGPT, allowing users to search and purchase items from external retailers—though no sponsored ads are included yet. The system uses user preferences and reviews to generate recommendations.
Brief: Meta has unveiled its AI chatbot, built on the Llama 4 model, offering voice-first interactions and deep integration with WhatsApp, Instagram, and Facebook, though opting out of data collection remains difficult.
Brief: The new Meta AI app includes a discover feed showing how friends use the chatbot, with privacy controls, but default settings heavily favor data sharing for AI training.
Brief: Sam Altman introduces a new mobile verification device, aiming to enhance security and authentication in the tech space, though details remain scarce due to service disruptions.

This week’s coding challenge:
This week’s tip:
Use Rust's derive macros with custom attributes to generate flexible, type-safe database mappings that enforce compile-time schema validation. This pattern leverages Rust's trait system to automatically implement database serialization with custom field mappings and validations.

Wen?
Complex schemas: When working with databases that have strict typing requirements or complex JSON/JSONB fields.
Migration-heavy projects: Ensures schema changes are caught at compile-time rather than runtime.
Multi-tenant systems: Enforce schema isolation and validation rules across different database contexts.
I was wise enough to never grow up while fooling most people into believing I had.
Margaret Mead


That’s it for today! ☀️
Enjoyed this issue? Send it to your friends here to sign up, or share it on Twitter!
If you want to submit a section to the newsletter or tell us what you think about today’s issue, reply to this email or DM me on Twitter! 🐦
Thanks for spending part of your Monday morning with Hungry Minds.
See you in a week — Alex.
Icons by Icons8.
*I may earn a commission if you get a subscription through the links marked with “aff.” (at no extra cost to you).